Perils of running your own server
A couple of days of this site being up and I've already made some friends.
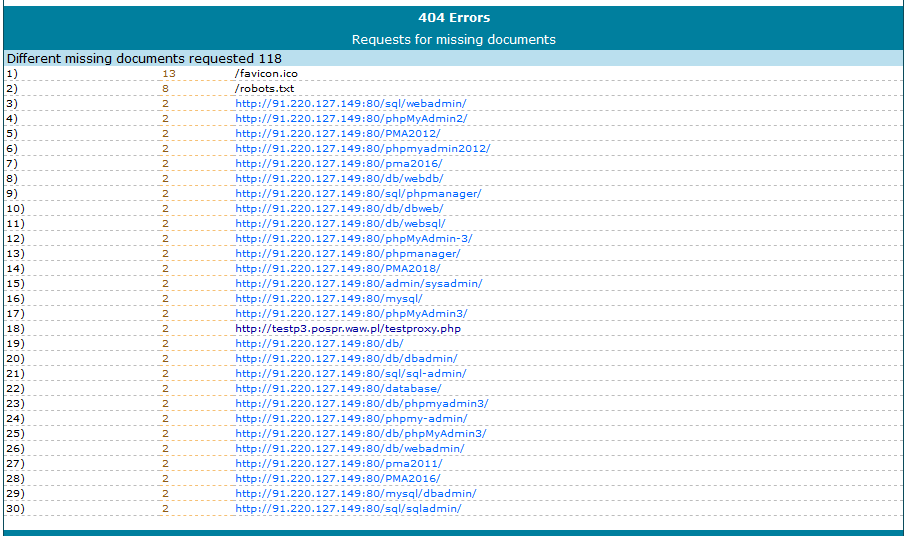
I used a simple lighttpd log analyzer called Visitors (that apparently was written by antirez of Redis fame!) to see who was actually looking at my website, and why.
And of course besides a couple visits from people who got here from Facebook and a dozen visits from myself to bump up the numbers, there was someone with a Japanese IP probing around for various Web control panels on all the URLs people usually put their control panels on.
How did this happen? My guess is there's a bot somewhere that sends out HTTP GET requests to everything in a given IP address range (note they didn't use a domain name) -- if the host responds with a nice page, it can then probably try poking one of the hundreds of vulnerabilities that say phpMyAdmin has.
So this is one of the benefits of this blog being just a static set of HTML files generated from some Markdown.
This is sort of similar to when one has sshd running with the default settings on a publically-routable machine and then gets really surprised when their authentication logs show hundreds of attempts per day to ssh in as root. This is why people recommend changing the SSH port from the default one -- not because it boosts security, but because it reduces the number of nuisance entries in the log.
There aren't many of these and I'm enjoying the company for now, but I'm considering redirecting requests to these URLs to something naughty. And would have I been able to see and enjoy all of this if I just popped my blog on GitHub Pages or something?